Check out my first novel, midnight's simulacra!
RDRAND: Difference between revisions
(link to idf slide) |
No edit summary |
||
| (One intermediate revision by the same user not shown) | |||
| Line 9: | Line 9: | ||
** Each seed requires at least two healthy values (per-sample result) | ** Each seed requires at least two healthy values (per-sample result) | ||
** "In the rare event a DRNG fails at runtime, it will cease to issue random numbers" | ** "In the rare event a DRNG fails at runtime, it will cease to issue random numbers" | ||
*** There seems no way to detect this situation save executing RDRAND and seeing CF unset. | |||
* "Built-in Self Tests" | * "Built-in Self Tests" | ||
** DRNG is run for 256 samples of OHT validation before being made available to software | ** DRNG is run for 256 samples of OHT validation before being made available to software | ||
** OHT is provided known-bad data and must identify it as "unhealthy" | ** OHT is provided known-bad data and must identify it as "unhealthy" | ||
** Deterministic values are played through the conditioner, and results are verified | ** Deterministic values are played through the conditioner, and results are verified | ||
==Limitations== | ==Limitations== | ||
"The one use case that it is cryptographically insufficient for is to seed a new PRNG, which probably means it is unsuitable for being fed as-is into /dev/random." - [http://www.spinics.net/lists/linux-crypto/msg05883.html H. Peter Anvin], 2011-06-14 | "The one use case that it is cryptographically insufficient for is to seed a new PRNG, which probably means it is unsuitable for being fed as-is into /dev/random." - [http://www.spinics.net/lists/linux-crypto/msg05883.html H. Peter Anvin], 2011-06-14 | ||
| Line 18: | Line 20: | ||
* Intel's [http://software.intel.com/en-us/articles/download-the-latest-bull-mountain-software-implementation-guide/ Bull Mountain Software Implementation Guide] | * Intel's [http://software.intel.com/en-us/articles/download-the-latest-bull-mountain-software-implementation-guide/ Bull Mountain Software Implementation Guide] | ||
* IEEE Spectrum's September 2011 article, [http://spectrum.ieee.org/computing/hardware/behind-intels-new-randomnumber-generator "Behind Intel's New Random-Number Generator"] | * IEEE Spectrum's September 2011 article, [http://spectrum.ieee.org/computing/hardware/behind-intels-new-randomnumber-generator "Behind Intel's New Random-Number Generator"] | ||
== | ==Corrections== | ||
* David Johnston of Intel corrected me on 2011-09-15: "RDRAND is not an [[AVX]] instruction. It is a normal instruction." Thanks, David! | * David Johnston of Intel corrected me on 2011-09-15: "RDRAND is not an [[AVX]] instruction. It is a normal instruction." Thanks, David! | ||
[[CATEGORY: X86]] | [[CATEGORY: X86]] | ||
Latest revision as of 01:49, 24 January 2012
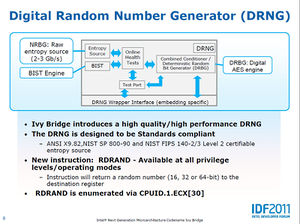
RDRAND is an instruction available on Intel processors for which CPUID sets bit 30 of the ECX register high (starting with Ivy Bridge). It is available at all privilege levels, and generates 16-, 32- or 64-bit random integer values (64-bit only in long mode). Its single operand is the (general-purpose) destination register. It sets the CF bit of EFLAGS to 1 if the destination register has been successfully set. Bull Mountain (the DRNG hardware + RDRAND instruction) is said to leverage "NIST SP800-90, FIPS-140-2, and ANSI X9.82." The Bull Mountain hardware is per-processor package. H. Peter Anvin added support to the Linux kernel 2011-07-29. It is expected to soon be used by OpenSSL.
DRNG Implementation
- A "nondeterministic hardware process" provides a 3Gbps entropy source as paired 256-bit values...
- which are distilled through a FIPS-197/NIST SP800-38A AES/CBC-MAC conditioner, yielding single 256-bit values...
- which seed a "~6Gbps" NIST SP800-90 AES-CTR, computing "not more than 511 128-bit values per seed."
- "Online Health Tests" test the entropy source against mathematical models per-sample and at a 64k window
- Each seed requires at least two healthy values (per-sample result)
- "In the rare event a DRNG fails at runtime, it will cease to issue random numbers"
- There seems no way to detect this situation save executing RDRAND and seeing CF unset.
- "Built-in Self Tests"
- DRNG is run for 256 samples of OHT validation before being made available to software
- OHT is provided known-bad data and must identify it as "unhealthy"
- Deterministic values are played through the conditioner, and results are verified
Limitations
"The one use case that it is cryptographically insufficient for is to seed a new PRNG, which probably means it is unsuitable for being fed as-is into /dev/random." - H. Peter Anvin, 2011-06-14
See Also
- Intel's Bull Mountain Software Implementation Guide
- IEEE Spectrum's September 2011 article, "Behind Intel's New Random-Number Generator"
Corrections
- David Johnston of Intel corrected me on 2011-09-15: "RDRAND is not an AVX instruction. It is a normal instruction." Thanks, David!