Check out my first novel, midnight's simulacra!
XDP: Difference between revisions
No edit summary Tags: mobile web edit mobile edit |
Tags: mobile web edit mobile edit |
||
| Line 28: | Line 28: | ||
===Modifying packet data=== | ===Modifying packet data=== | ||
Modifications should generally take place through the functions exposed in <tt>bpf-helpers(7)</tt>. Updating data in a TCP payload, for instance, requires recomputing a TCP checksum, which can done most effectively through these methods. <tt>bpf_redirect()</tt> and <tt>bpf_redirect_map()</tt> are used to set the destination of an <tt>XDP_REDIRECT</tt> operation. <tt>bpf_clone_redirect()</tt> allows a <i>clone</i> of a packet to be redirected, while retaining the original. | Modifications should generally take place through the functions exposed in <tt>bpf-helpers(7)</tt>. Updating data in a TCP payload, for instance, requires recomputing a TCP checksum, which can done most effectively through these methods. <tt>bpf_redirect()</tt> and <tt>bpf_redirect_map()</tt> are used to set the destination of an <tt>XDP_REDIRECT</tt> operation. <tt>bpf_clone_redirect()</tt> allows a <i>clone</i> of a packet to be redirected, while retaining the original. | ||
===Caveats=== | |||
There is significant (on the order of hundreds of bytes) overhead on each packet. Furthermore, until recently (5.18), or without driver support, XDP cannot use packets larger than an architectural page. On amd64 with 4KB pages, without the new "multibuf" support, only about 3520 bytes are available within a frame. This is smaller than many jumbo MTUs, and furthermore precludes techniques like LRO. With multibuf, packets of arbitrary size can pass through XDP. | |||
==AF_XDP== | ==AF_XDP== | ||
Revision as of 18:21, 4 December 2022
In the beginning, there were applications slinging streams through the packetizing Honeywell DDP-516 IMPs, and it was good. Then multiple applications needed the network, and needed it in different ways. Then the networks needed walls of fire, and traffic which was shaped. Some called for the Labeling of Multiple Protocols, and others called for timestamps, and still others wanted to SNAT and DNAT and also to masquerade. And yea, IP was fwadm'd, and then chained, and then tabled, and soon arps and bridges too were tabled. And behold now tables of "nf" and "x". And Van Jacobson looked once more upon the land, and frowned, and shed a single tear which became a Channel. And then every ten years or so, we celebrate this by rediscovering Van Jacobson channels under a new name, these days complete with logo.
Most recently, they were rediscovered under the name DPDK, but the masters of the Linux kernel eschewed it, and instead rediscovered them under the name XDP, the eXpress Data Path, expressed using eBPF programs. XDP was added to Linux 4.8 and has been heavily developed since then, and is often seen together with iouring, especially with the new AF_XDP family of sockets.
XDP is used to bypass large chunks of the Linux networking stack (including all allocations, particularly alloc_skb()), especially when dropping packets or shuffling them between NICs.
Using XDP
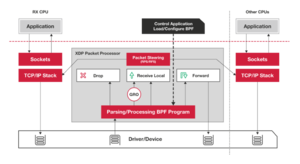
An XDP program is an eBPF program invoked for each received packet which runs either:
- early in the kernel receive path, with no driver support (Generic Mode)
- from the driver context following DMA sync, without any kernel networking stack touches (requires driver support) (Native mode)
- on the NIC itself, without touching the CPU (requires hardware+driver support) (Offloaded mode)
Offloaded mode can theoretically beat native mode, which will usually beat generic mode. XDP programs are specific to a NIC, and most easily attached using xdp-loader. Lower-level functionality is available from libxdp, and below that is pure eBPF machinery. Multiple XDP programs can be stacked on a single interface as of Linux 5.6 (multiprog requires BTF type information, created by using LLVM 10+ and enabling debug information). XDP is only applied to the receive path.
An XDP program can modify the packet data and perform limited resizes of the packet. It returns an action code:
- XDP_PASS: the packet continues through the network stack
- XDP_DROP: the packet is dropped
- XDP_ABORTED: indicate an error (the packet is dropped)
- XDP_TX: emit the packet back out the interface on which it was received
- XDP_REDIRECT: send the packet to another NIC or an AF_XDP socket
Think of XDP_ABORTED as returning -1 from the eBPF program; it's meant to indicate an internal error. Theoretically, the packet could continue through the stack (as it would have if no XDP program had been running), but XDP uses "fail-close" semantics. Edits to the packet are carried through all XDP paths.
xdp-loader status will list NICs and show any attached XDP programs.
Note that XDP runs prior to the packet socket copies which drive tcpdump, and thus packets dropped or redirected in XDP will not show up there. It's better to use xdpdump when interacting with XDP programs; this also shows the XDP decision made for each packet.
Modifying packet data
Modifications should generally take place through the functions exposed in bpf-helpers(7). Updating data in a TCP payload, for instance, requires recomputing a TCP checksum, which can done most effectively through these methods. bpf_redirect() and bpf_redirect_map() are used to set the destination of an XDP_REDIRECT operation. bpf_clone_redirect() allows a clone of a packet to be redirected, while retaining the original.
Caveats
There is significant (on the order of hundreds of bytes) overhead on each packet. Furthermore, until recently (5.18), or without driver support, XDP cannot use packets larger than an architectural page. On amd64 with 4KB pages, without the new "multibuf" support, only about 3520 bytes are available within a frame. This is smaller than many jumbo MTUs, and furthermore precludes techniques like LRO. With multibuf, packets of arbitrary size can pass through XDP.
AF_XDP
Getting these packets to userspace is best done with AF_XDP sockets. With driver support, this is a zero-copy operation. Routing to an AF_XDP socket is done via bpf_redirect().
See Also
External links
- Bringing TSO/GRO and Jumbo Frames to XDP, Linux Plumbers 2021